Here's netcat 1.11 compiled for both 32 and 64-bit Windows (but note that 64-bit version hasn't been tested much - use at your own risk).
I'm providing it here because I never seem to be able to find a working netcat download when I need it.
Small update: netcat 1.12 - adds -c command-line option to send CRLF line endings instead of just CR (eg. to talk to Exchange SMTP)
 Warning: a bunch of antiviruses think that netcat (nc.exe) is harmful for some reason, and may block or delete the file when you try to download it. I could get around this by recompiling the binary every now and then (without doing any other changes at all, which should give you an idea about the level of protection these products offer), but I really can't be bothered.
Warning: a bunch of antiviruses think that netcat (nc.exe) is harmful for some reason, and may block or delete the file when you try to download it. I could get around this by recompiling the binary every now and then (without doing any other changes at all, which should give you an idea about the level of protection these products offer), but I really can't be bothered. 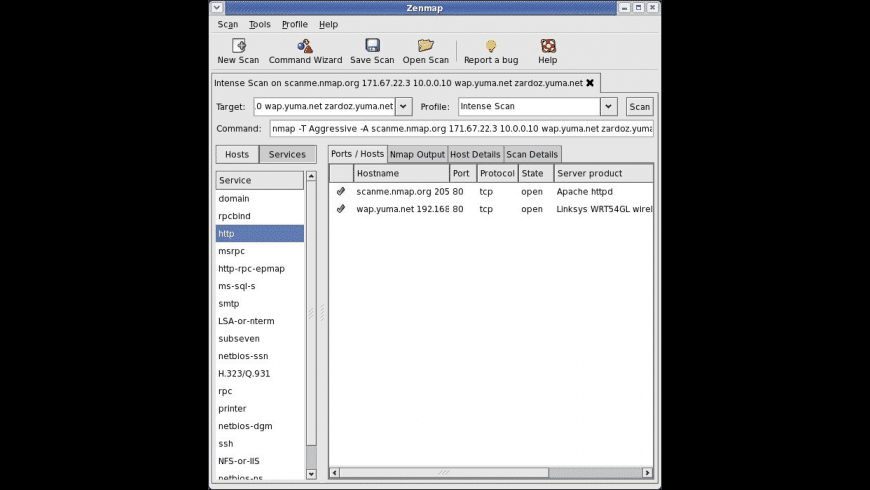
Netcat Tool In Kali Linux
Netcat is a computer networking utility for reading from and writing to network connections using TCP or UDP. Objective: Learn netcat tool by doing the following activities: Use netcat to listen on TCP port 4000 of the localhost. Open a new tab and use netcat to connect to the listening instance. Use netcat to listen on UDP port 4000 of the. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need, including port binding to accept incoming connections. The original Netcat was released by Hobbit in 1995, but it hasn't been maintained despite its popularity. Netcat 1.11 for Win32/Win64. Here's netcat 1.11 compiled for both 32 and 64-bit Windows (but note that 64-bit version hasn't been tested much - use at your own risk). I'm providing it here because I never seem to be able to find a working netcat download when I need it. Small update: netcat 1.12 - adds -c command-line option to send CRLF line.
What Is Netcat Used For


What Is A Netcat
Mar 25, 2021 Netcat functions as a back-end tool that allows for port scanning and port listening. In addition, you can actually transfer files directly through Netcat or use it as a backdoor into other networked systems. Partnered with a tool like Varonis Edge, you would receive an alert of any unusual activity and could then use Netcat to investigate. Netcat is not considered the best tool for this job, but it can be sufficient (a more advanced tool is nmap) nc -v -n -z -w 1 192.168.1.2 1-1000 The -n parameter here prevents DNS lookup, -z makes nc not receive any data from the server, and -w 1 makes the connection timeout after 1 second of inactivity.