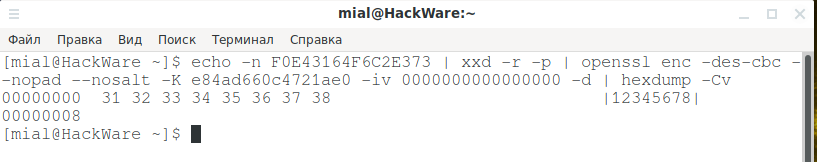
Crack or Decrypt VNC Server Encrypted Password 8 Websites to Help Identify Good or Bad StartUp Programs 3 Tools to Decrypt and Recover Passwords Saved in Firefox 5 Websites to Recognize Chinese Characters by Drawing with Mouse 7 Websites with Free User Guides, Service Manuals and Datasheets. Oct 07, 2019 Crack atau Decrypt VNC Server Encrypted Password Virtual Network Computing atau kebanyakan orang menyebutnya VNC adalah sistem untuk mengendalikan komputer dari jarak jauh seolah-olah Anda duduk di depan PC walaupun Anda jauh dari itu. The VNC Password Decoder (vncpwd) tool by Luigi Auriemma can decrypt classic VNC DES encryption method. Simply embed the encrypted password after the command line tool and the real password will be displayed. To use vncpwd, click Start button, type cmd at search bar and press Enter. Transport mechanism for encrypted data. They explicitly do not enjoy a privileged security position. The ultimate responsibility for authorizing remote access lies solely with VNC Server. When making a direct connection, VNC Viewer uses a direct TCP connection to VNC Server, performing no interaction with RealVNC cloud services at all. VNC Password Recovery is the FREE software to instantly recover VNC password stored by popular VNC Servers. It automatically detects the encrypted VNC password stored in the file system or registry by various VNC server applications. While VNC implements some sort of encryption for the login process, it's not fully secure and the login password.
If you're new to Linux or Unix, you might prefer using a graphical user interface (GUI) over the command-line interface (CLI), and when remotely connecting you can use the remote desktop protocol and GUI-based Virtual Network Computing (VNC).
Some Linux distros come with a VNC server pre-installed and for others you'll probably find plenty of tutorials on how to get started, so we'll skip the basics and share some security tips. As a result, for this tutorial we assume you already have a VNC server installed and running on a Linux/Unix machine.
Securing VNC with SSH

This utility will allow you to fetch and decrypt VNC passwords on a local computer system with VNC Server configured with a password. It works by fetching the encrypted password in the registry then decrypting it using the DES algorithm. VNC Password Recovery is the FREE software to instantly recover VNC password stored by popular VNC Servers. It automatically detects the encrypted VNC password stored in the file system or registry by various VNC server applications.
While VNC implements some sort of encryption for the login process, it's not fully secure and the login password could be sniffed and cracked by people on the local network or Internet. Plus the actual VNC sessions aren't encrypted at all.
To fully secure your VNC sessions you can tunnel the traffic through a SSH connection to the server. To do so, you'll first want to set up an SSH server and open the SSH port 22 on the machine you're trying to remotely access. Then on the computer you're remotely connecting from you can set up a port forward in the SSH client.

Here's how you'd configure the port forward when using the PuTTY SSH client:
- Enter your host name or IP of the SSH server and select the private key file like normal.
- Next, navigate to Connection > SSH > Tunnels.
- For the Source Port, enter the port that you want to use when connecting via VNC over SSH on the local machine. You probably want to use '5900' -- the default port used by clients -- which means you don't need to specify a port when connecting via the VNC client.
- For the Designation Port, enter 'localhost:' and the port for the VNC display/session you want to connect to, which is likely '5901' -- so in this case you'd enter 'localhost:5901'
- Click the Add button.
- If you'd like to save the connection settings, navigate back to the Session settings and click the Save button.
Now you can connect to your server via SSH, and while connected you can open your VNC client and connect to 'localhost.' Once successful, you may want to consider closing the VNC port (probably 5901) on your Linux machine if you had previously connected directly via the Internet.
Changing the VNC Password
If you'd like to change your VNC server's password in Linux you can use the vncpasswd command, which is the same command that's run by the vncserver script the first time you start a VNC desktop. This command will change and/or store an obscured version of the password to the password file by default at HOME/.vnc/passwd.
Since it's not securely encrypted, keep in mind that anyone with access to the password file could convert it to plain text and reveal the password.
When you're ready to change the password, enter the following command in the Terminal, either on the machine directly or remotely using a SSH client like PuTTY:
You'll be prompted twice to enter the new password, which should be between six and eight characters long. Then restart the VNC server by killing the VNC session/display:
Then you can start the VNC session or display again by entering:
Eric Geier is a freelance tech writer. He's also the founder of NoWiresSecurity, which provides a cloud-based Wi-Fi security service for businesses, and On Spot Techs, which provides on-site computer services.
Follow ServerWatch on Twitter and on Facebook
SAS Metadata Bridges
SAS Metadata Bridges are available through the software offerings SAS Enterprise Data Integration Server and SAS Data Integration Server. You can use SAS Metadata Bridges to import and export metadata through SAS Management Console or SAS Data Integration Studio, which are components in these offerings.
- Publisher: SAS Institute Inc.
- Home page:support.sas.com
- Last updated: April 29th, 2012
Password Decrypt
Password decrypter is a Windows-based programs thatallow user to enter a Cisco Type 7 decrypted password, and the program will immediately return the clear-text password. User simply needs to cut and pastes the encrypted password into the dialog box;the decoder will do the rest.
Or Decrypt Vnc Server Encrypted Password Tool
- Publisher: Secure Bytes
PDFdu PDF Password Remover
PDFdu PDF Password Remover is a program that can be used to decrypt password-protected Adobe Acrobat PDF files. It can help you generate PDF files with no password from the original PDF files which are not permitted to be edited, changed, printed, copied, added annotations. You can remove user password, owner password and restrictions of no-printing, no-copying and no-editing from PDF files.
- Publisher: PDFdu
- Home page:www.pdfdu.com
- Last updated: February 24th, 2015
Johnny
Or Decrypt Vnc Server Encrypted Password Free
Johnny's aim is to automate and simplify the process with the help of the tremendously versatile and robust John the Ripper, as well as add extra functionality on top of it, specific to Desktop and GUI paradigms, like improved hash and password workflow, multiple attacks and session management.
- Publisher: Aleksey Cherepanov
- Home page:openwall.info
- Last updated: September 29th, 2016
Easy Excel Password Recovery Free
Forgotten your Microsoft Excel password and can't open your file? Use Easy Excel Password Recovery.Free to free recover lost or forgotten Excel workbook or worksheet protected passwords to open or modify your files. Wizard user-friendly interface helps you to find the best way to decrypt password.
- Publisher: Officeconvert Software, Inc.
- Home page:www.officeconvert.com
- Last updated: June 22nd, 2011
MgoSoft PDF Security
With PDF Encrypt that can help you set open passwords for your PDF files, preventing the PDF files from opening or reading. You can also use this tool to set owner passwords, preventing your PDF files from printing, editing, copying, and changing. Mgosoft PDF Security does NOT require Adobe Acrobat or any other Adobe products.
- Publisher: mgosoft.com
- Home page:www.mgosoft.com
- Last updated: May 31st, 2018
FoxPDF PDF Password Remover
FoxPDF PDF Password Remover is a program that can decrypt password-protected Adobe Acrobat PDF files. The program allows you to remove restrictions on printing, editing, copying. It also enables you to remove the security settings from your encrypted PDF file.
- Publisher: FoxPDF Softwre Inc
- Home page:www.foxpdf.com
- Last updated: May 27th, 2013
MD5 Password
MD5 Password is a password recovery tool for security professionals, which can be used to decrypt a password if its MD5 hash is known. MD5 is an industry standard hash algorithm that is used in many applications to store passwords.Key Features:* Fast, highly optimized recovery engine (supports multi-core, multi-CPU, hyperthreading)
- Publisher: LastBit Software
- Last updated: September 29th, 2011
Wi-Fi Password Recovery
Many times, when we format or uninstall updates from our system, we also lost the Wi-Fi password we use to connect to the Internet. This program allows us to recover this password using a variety of adjustable parameters.Please note that the program is not very easy to use for casual users. You need to check the Help file and follow closely the instructions to obtain good results.
- Publisher: SmartKey, Inc.
- Home page:www.recoverlostpassword.com
- Last updated: March 11th, 2017
PDF Password Unlocker
The standard security provided by PDF consists of two different methods and two different passwords. P-41r kitagawa air purity test kit price. A PDF document may be protected by password for opening ('user' password) and the document may also specify operations that should be restricted.
- Publisher: Password Unlocker Studio
- Last updated: November 11th, 2009
A-PDF Restrictions Remover
Once installed on your PC, this small application will integrate in Windows Explorer and offer you two easy ways to decrypt any protected PDF file. You can either remove the restrictions from the PDF files or you can opt for the Remove Restrictions & Save as option.
- Publisher: A-PDF
- Home page:www.a-pdf.com
- Last updated: November 25th, 2012
Accent OFFICE Password Recovery
Accent OFFICE Password Recovery attempts to recover passwords of MS Office documents using brute force, mask, and dictionary attacks. It supports documents created by MS Office (versions up to 2016), OpenOffice 4, and LibreOffice 6. Word 97/2000 passwords can be recovered instantly.
- Publisher: Passcovery Co. Ltd.
- Home page:passwordrecoverytools.com
- Last updated: December 12th, 2018
Vnc Server Set Password
Asterisk Password Decryptor
Asterisk Password Decryptor is a powerful tool to recover lost or forgotten passwords. It allows you to reveal the hidden passwords on password dialog boxes and web pages that are hidden by the row of asterisk. You can simply drag the icon to any password box to find the real password hidden by the asterisks.
- Publisher: KRyLack Software
- Home page:www.krylack.com
- Last updated: April 4th, 2012
Facebook Password Decryptor
Facebook Password Decryptor is a software tool that instantly recovers your lost Facebook password stored by popular web browsers and messengers. The program support recovering multiple Facebook accounts stored with any of the supported applications. You can save the recovered Facebook password list to HTML/XML/TEXT/CSV file for transferring to other system or for future use.
- Publisher: SecurityXploded
- Home page:securityxploded.com
- Last updated: April 30th, 2015
Jihosoft iTunes Backup Unlocker
Jihosoft iTunes Backup Unlocker is a utility designed to recover iPhone/iPad/iPod backup passwords and enable access to an iTunes backup file. You can recover lost or forgotten passwords of encrypted iTunes backups; decrypt iTunes backup passwords for all iPhone, iPad, and iPod devices; recover iPhone backup passwords; regain access to iTunes backup data, and more.
- Publisher: Jihosoft Studio
- Home page:www.jihosoft.com
- Last updated: July 12th, 2018
StorageCrypt
When working in a high-risk environment, the safety of your data is absolutely crucial. A suitable solution to this issue could come from an advanced drive encryption tool; for instance, you can try StorageCrypt.Being unfamiliar with this type of program won't be a problem, as the application will bring you the easiest way to password-protect and decrypt any drive.
- Publisher: Magiclab
- Home page:www.magic2003.net
- Last updated: February 19th, 2011
Hash Kracker
Hash Kracker is the free all-in-one tool to recover a hash password for multiple hash types. It uses dictionary-based recovery method which makes the operation simple and easy. You can use tools like Crunch, Cupp to generate a brute-force or custom password list file and then use it with 'Hash Kracker'.
- Publisher: SecurityXploded
- Home page:securityxploded.com
- Last updated: March 14th, 2016
Mail Password Decryptor
Mail Password Decryptor can recover saved passwords from popular email clients including Outlook, Outlook Express, Thunderbird, Windows Live Mail, IncrediMail, The Bat!, and messengers such as GTalk, Pidgin, and Miranda Messenger. After recovery, you can save the password list as HTML/XML/Text/CSV files.
Decrypt Cisco Encrypted Password
- Publisher: SecurityXploded
- Home page:securityxploded.com
- Last updated: March 25th, 2017
Vnc Server Source Code
You create a RealVNC® account when you purchase VNC® Connect, or take a trial.
Your RealVNC® account credentials (email address and password) are important; please do not share them with anyone! You need them them each time you:
- Sign in online to manage your team, subscription and more.
- Sign in to VNC Server to apply your subscription to remote computers (if you have device access).
- Sign in to VNC Viewer to remotely access computers (both device access and instant support).
Your account password must be at least 8 characters long and should not be the same as a VNC Server password, nor that of any other online service you use.
Note that if you invite someone in to your team to share remote access, that person sets up their own RealVNC® account in the process of accepting your invitation. They never need to know your RealVNC® account credentials.
We strongly recommend enabling 2–step verification on the Security page of your RealVNC® account.
Every remote control session must be authenticated before it can begin.
- If you have device access, connecting users must authenticate to VNC Server, an app installed as part of VNC® Connect on every remote computer. There are many different authentication schemes, and multi-factor authentication is available. More information.
- If you have instant support, an end user enters a 9-digit code unique to the session, received from their support technician out-of-band. It's not possible for anyone else to connect in.
Yes. We recommend setting it up.
Everyone should enable 2-step verification for their RealVNC® account on the Security page. See how to do this.
If you have device access, we also recommend enabling multi-factor authentication for VNC Server, an app installed as part of VNC® Connect on every remote computer. See how to do this.
Yes, always.
If you have a Home or Professional subscription, connections are encrypted end-to-end using 128-bit AES, 2048-bit RSA keys and perfect forward secrecy, so sessions are entirely private to you now and in the future.
If you have an Enterprise subscription, you have the option to upgrade to 256-bit AES. To do this:
- Open the VNC Viewer app, and navigate to File > Preferences > Expert.
- Search for the Encryption parameter and set the value to
AlwaysMaximum.
Follow the instructions below.
- Buy an Enterprise subscription.
- When creating your RealVNC® account, choose a complex, unique password (not one you use for any other online service).
- Enable 2-step verification for your RealVNC® account on the Security page online.
- If you wish to share remote access, only invite people you trust in to your team.
- Mandate 2-step verification for all these people as well on the Security page.
- If you have device access, additionally follow these instructions.
Security is at the heart of our business so we publish information about potential vulnerabilities as soon as we find them.
We do not record your sessions, and never store remote computer passwords. We don’t store payment or credit card information either; that’s stored on our behalf by a PCI DSS-compliant vendor (Braintree).
We do store certain data in the following circumstances:
- If you enable analytics when installing VNC Viewer.
- If you have device access and enable either analytics or update notifications when installing VNC Server.
- If you have device access and sign in to VNC Viewer on multiple devices in order to sync your address book.
- If you have instant support, note we automatically record certain session events for review purposes.
See our privacy policy for what data is collected and where it is stored.
If you don’t want RealVNC® to store any data at all then you must:
- Buy an Enterprise subscription.
- Only enable device access (that is, install VNC® Connect on computers you own or manage).
- Only establish direct connections to those computers.
- Disable analytics and update notifications for both VNC Viewer and VNC Server.
- Connect using VNC Viewer without signing in to it (your address book will not sync between devices).
Only people you invite in to your team can sign in to VNC Viewer and discover your computers (so only invite people you trust!). Note with a Professional or Enterprise subscription you can further restrict discovery by assigning permissions on the Computers page of your RealVNC® account to precisely match computers with people.
If a person cannot discover your computers then they cannot possibly establish cloud connections to them; there’s no way to bypass our discovery service.
Note that if you have an Enterprise subscription and intend to establish direct connections, it is possible for a malicious entity to sniff the port you’ve opened in the remote computer’s firewall (5900 TCP by default). It’s much safer to use cloud connectivity over the Internet!
Only people in your team with permission to discover computers can sign in to VNC Viewer and attempt to connect to them.
To complete a connection, a team member must still enter the credentials expected by VNC Server running on that computer.
So computers are protected twice, by independent password mechanisms: the RealVNC® account system controls discovery, and the VNC Server authentication scheme polices connectivity.
VNC Server has a unique digital signature designed to help keep you safe online. This is a hexadecimal representation of a 2048-bit RSA public key hash, which (in the real world) means it’s a six-word memorable catchphrase, for example “Omega Chris Chicago. Alabama arrow network”. Download our whitepaper for the technical details.
When you connect, the RealVNC® services automatically verify this identity, and VNC Viewer additionally prompts you to check it yourself. If you’re subsequently warned that the catchphrase has changed, it might indicate that someone has tampered with the computer, or is trying to intercept your connection (a ‘man-in-the-middle’ attack).
Note that if you have an Enterprise subscription and establish a direct connection, then the RealVNC® services cannot perform this automatic check, so you should do so yourself.
Yes. VNC Server password-protection is turned on permanently.
VNC Server's authentication scheme is completely separate from your RealVNC® account, so even if a malicious entity learns your account credentials and signs in to VNC Viewer as you, they still cannot connect. And if they try to guess the VNC Server password (a 'brute force' or 'dictionary' attack), they’ll be blacklisted.
Note you can ask VNC Viewer to remember VNC Server passwords for you as a convenience. If you do, we recommend setting a master password on VNC Viewer's Preferences > Privacy page.
If you have a Home subscription, there’s only one VNC Server authentication scheme. Make sure the password you’re prompted to create when you install VNC Server is difficult to guess, and keep it safe. You must specify at least 6 case-sensitive letters, numbers, and special characters such as
!@*#&,though we recommend more (the maximum is 255).If you have a Professional or Enterprise subscription, then by default VNC Server is integrated into the credentialing mechanism of the remote computer, so you don’t have to create or remember yet another password. Simply connect using the same user name and password you normally use to log on to your user account on that computer. You can register other users with VNC Server so they can connect using their own familiar system account credentials if you wish.
If you have a Professional or Enterprise subscription, you can change the default system authentication scheme to specify multi-factor authentication for VNC Server.
If you have an Enterprise subscription and a suitable corporate network, you can set up single sign-on (SSO) for VNC Server.
The first time you use VNC Viewer to connect to a computer, you must enter the password expected by VNC Server.
Subsequently, you can ask VNC Viewer to remember this password so you don’t have to enter it each time. If you do, we additionally recommend setting a master password for VNC Viewer in case you lose or share your device:
VNC Viewer stores passwords locally and never syncs them to other devices via our cloud service (so you’ll have to remember them on each device you connect from). Download our whitepaper for the technical details.
Note you can sign out remotely from all VNC Viewer devices if you think your account has been compromised. Sign in to your RealVNC® account and navigate to the Security page.
Yes. VNC Server automatically logs audit information, so you have a complete record of who’s connected, when, from where and, if the user successfully authenticated, the time of disconnection (so you can calculate session length).
The storage destination for this information differs depending on the platform and VNC Server mode. General information about logging is available here.
Note you can quickly dial up the logs to debug level if you need.
Yes. If you will be physically present at the computer when people connect, you can configure VNC Server to notify you and approve or reject each connection:
Please note: The Connection Request dialog box will not be shown in the VNC Server UI when a user with admin rights to that computer connects to it.
To do this, turn on Show accept/reject prompt for each connection on VNC Server's Options > Connections page:
You can disconnect all users immediately:
...or individually from VNC Server's Information Center dialog.
By default, users can connect concurrently. You can specify that only one user connects at a time.
By default, if a connecting user fails to authenticate properly five times in a row, their computer is blacklisted. You can lower this threshold for additional protection from brute-force or port scanning attacks.
If you have an Enterprise subscription and establish direct connections, you can filter incoming computers to prevent connections from particular IP addresses:
Yes. You can make sessions view-only for everyone on VNC Server’s Options > Users & Permissions page:
If you have a Professional or Enterprise subscription, you can exercise more fine-grained control and make sessions view-only just for some.
Alternatively, VNC Viewer users can choose to make their own sessions view-only from VNC Viewer's Properties dialog or mobile app toolbar.
Yes, if you have a Professional or Enterprise subscription.
You can register any number of users or groups (perhaps from your corporate network) with VNC Server:
You can then grant specific permissions to each. So for example you could grant system administrators full remote access, members of the group ‘teachers’ sufficient permissions to control the remote computer but not to transfer files or print, and make members of the group ‘pupils’ view-only.
If you have a Home subscription, all connected users have the same global permissions, though you can turn individual features off for everyone, or make all connections view-only, if you wish. It will also apply to you though!
You can blank the screens of most Windows computers (up to and including Windows 10). This is 'curtain mode' - equivalent to turning the monitor(s) of a remote computer off so people in the vicinity can't see what you're doing.
Screen blanking is hardware-dependent for Windows 8 and 10, so we recommend testing those systems first to make sure screen blanking will be effective:
For Windows 7 and earlier, most hardware should be supported. For Windows 8 and 10, most desktop screens manufactured after 2011 should be supported, including major manufacturers such as Dell and Samsung. Unfortunately, there is not as much support for laptop screens. Assuming your desktop screen was manufactured after 2011, try the following if the screen blanking test fails:
- Remove any base stations, splitters or repeaters used to connect your screens.
- Update your graphic card driver software to the latest version.
- If there is an option on the screen’s setup menu called MCCS or DDC/CI, enable that option.
You can prevent the keyboard and mouse of the remote computer being used by whoever wanders past while you're remotely connected to it:
You can configure VNC Server to automatically lock or log out from a Windows or Mac computer when you disconnect:
Of course, you can always lock or log out during your remote control session. Just don’t power the remote computer off, or you’ll be disconnected until someone turns it on again!
First, follow the general instructions for RealVNC® accounts here.
Then, follow the additional instructions below. Note you can perform bulk operations on computers remotely using policy, which has the additional security benefit of locking down those computers, preventing change by local users.
- In your RealVNC® account online, assign permissions on the Computers page to restrict discovery appropriately.
- On each remote computer:
- Install VNC® Connect in a secure location (such as
C:Program Files), and turn on update notifications. - Upgrade to 256-bit AES session encryption.
- Turn off direct connectivity. Only establishing cloud connections means no holes need be opened in firewalls.
- Enable multi-factor authentication for VNC Server.
- Restrict session permissions appropriately, perhaps to make particular users view-only.
- Harden blacklisting.
- If the owner will be physically present to approve connections, turn on query connect.
- Lock the remote desktop when the last user disconnects.
- Review connection logs on a regular basis.
- In your RealVNC® account online, assign permissions on the Computers page to restrict discovery appropriately.
VNC Viewer requests a session code each time a technician starts an instant support session, and RealVNC's services automatically generates a 9-digit code unique to the session.
This code is valid for 10 minutes. In that time, the technician must communicate it out-of-band so the end user can start the session.
The code expires either when it is used, or after 10 minutes, whichever comes first.
No. Only the technician generating a session code can connect to and control a computer that is owned by the recipient of the code.
However, as soon as a session starts, session event data is logged and stored online. If you have an Enterprise subscription, you can drill down into an individual session in order to review chat transcripts, file transfer activity, whether the technician elevated to perform administrative operations, and whether the technician rebooted the remote computer.
Every session is logged and a session history stored online.
If you have an Enterprise subscription, you can drill down into an individual session on the Sessions page of your RealVNC® account and review a detailed activity log. The following activity is recorded:
- Session start and end times
- File transfer operations
- Elevation requests
- Reboot attempts
- Chat transcripts
Note that chat transcripts are encrypted-at-rest on RealVNC’s servers. Privacy policy.